07. Course Outline
Course Outline Heading
Course Outline
ND545 C02 L00 A08 Course Outline
Course Outline Summary
Course Learning Objectives
At the end of this course a student will be able to:
- Apply best practices of Defense in Depth to secure computer systems (operating systems, networks, applications).
- Use the outputs from previous security events to analyze and improve future network security.
- Create ruleset changes to address network security issues.
- Search internal systems to determine network vulnerabilities.
- Recommend mitigations to address common application vulnerabilities.
- Encrypt and decrypt files.
- Recommend the appropriate encryption technique for securing data at rest and in transit.
- Create and deploy a strategy to harden Windows OS and Linux using Microsoft/NIST/compliance recommendations.
Course Outline Image
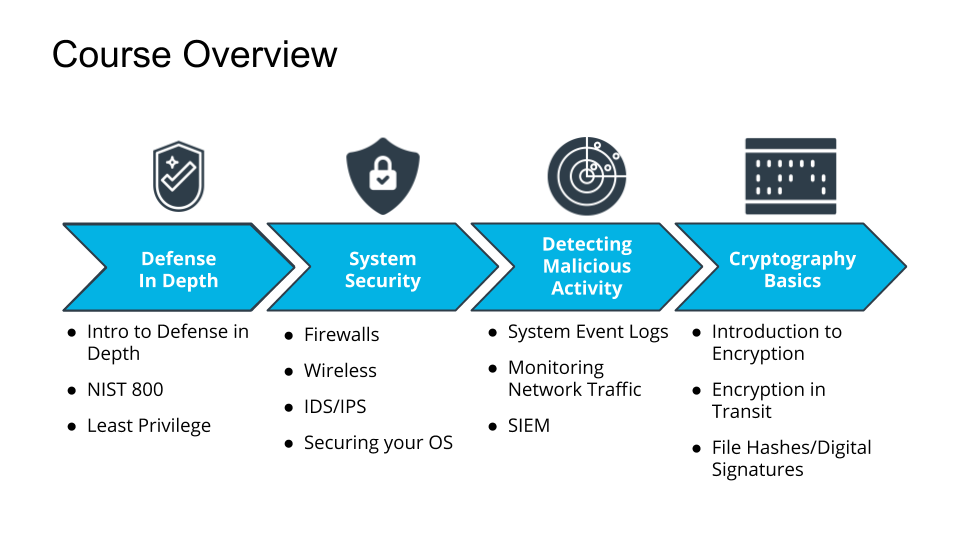
Course Overview